Blog posts
-

Security knowledge entropy
Entropy has been described as the measure of disorder of a system. The Second Law of Thermodynamics, as defined by Rudolf Clausius, states that the ‘Entropy of the universe tends to a maximum’, which means that the universe is heading towards maximum entropy, or maximum disorder. Entropy can be seen in everyday life, ice melts,…
-
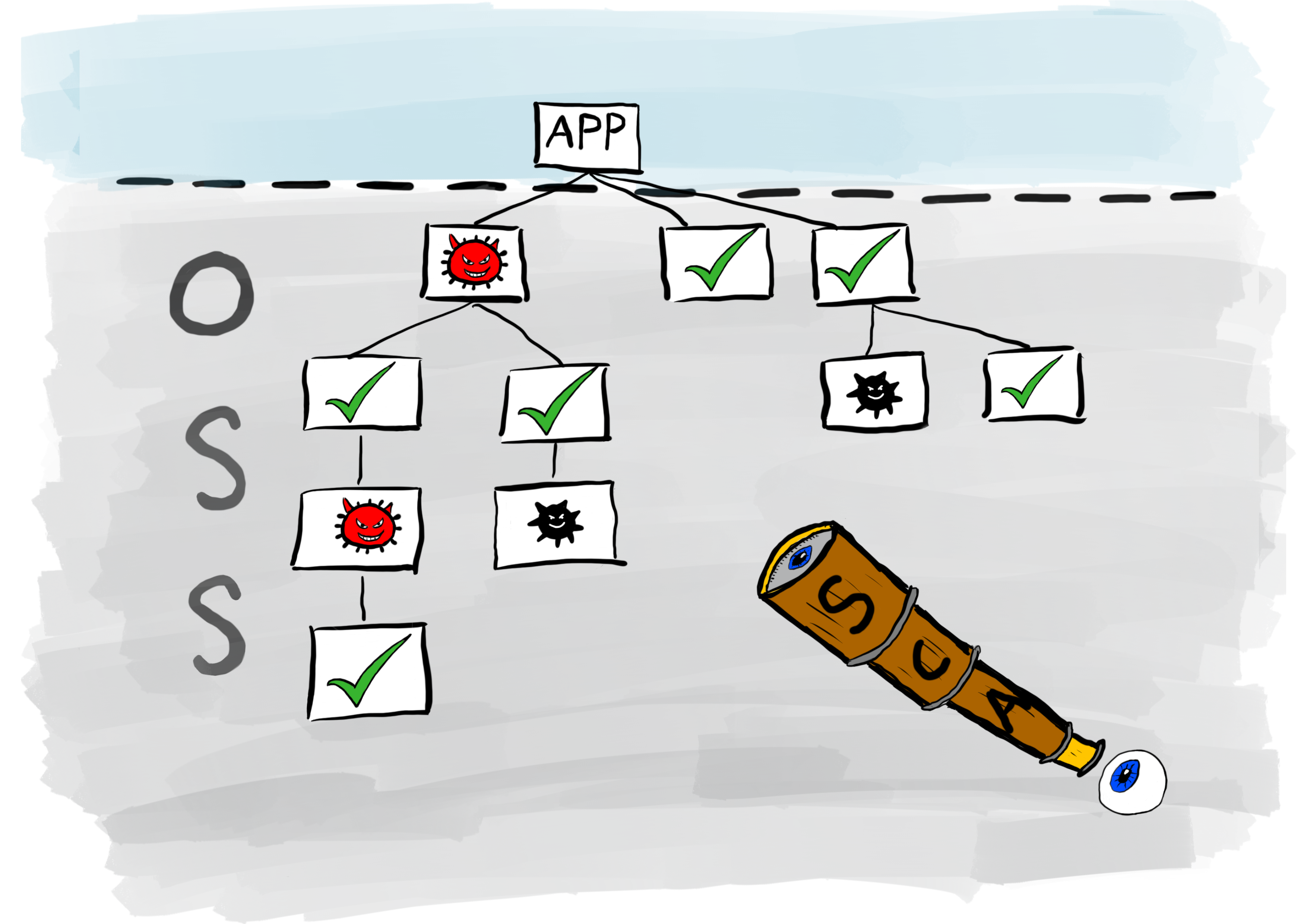
Security test automation part 5: SCA
In this final instalment of articles exploring security test automation, I take a closer look at Software Composition Analysis (SCA). Open source software has grown considerably over the last few years. As engineers struggle with the writing of code that meets ever-increasing demands of the business, they do not want the distraction of writing logic…
-

Security test automation part 4: RASP
In previous articles, I wrote about the Application Security Testing tools SAST, DAST and IAST, which are designed to help engineers fix problems during the development lifecycle. In this article, I write about a technology designed to protect applications in a production environment. This technology is known as Runtime Application Self-Protection (RASP). Once an application…
-
Security test automation part 3: IAST
In my previous two articles in this series on security test automation, I gave a brief insight into SAST and DAST. In this article I take a closer look at Interactive Application Security Testing (IAST), a relative newcomer to the security test automation scene. The key difference between IAST and the two previous types of…
-
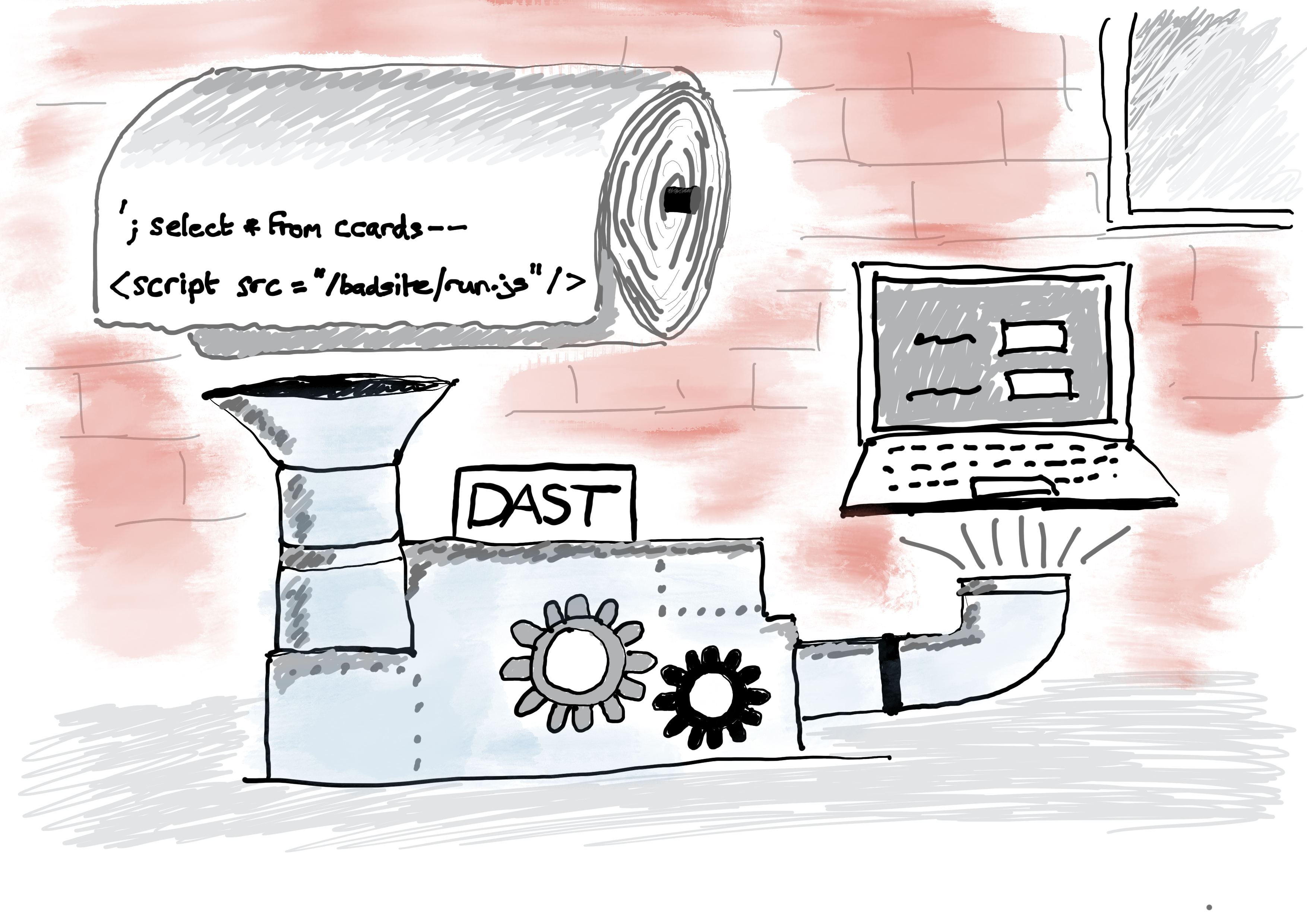
Security test automation part 2: DAST
In part one of this series of articles, I wrote about Static Application Security Testing (SAST). In this second part, I turn my attention to Dynamic Application Security Testing (DAST). Unlike SAST which analyses static application source code, DAST analyses the application dynamically while it is running. Immediately, this pushes the operation of the dynamic…
-
Security test automation part 1: SAST
A question that comes up frequently in my capacity as a DevOps / Agile Security consultant is: how do we integrate security test automation into our environments. There is a lot of information on automated security testing tools, but unfortunately, the vast majority of it is written by the companies who produce and sell the…
-

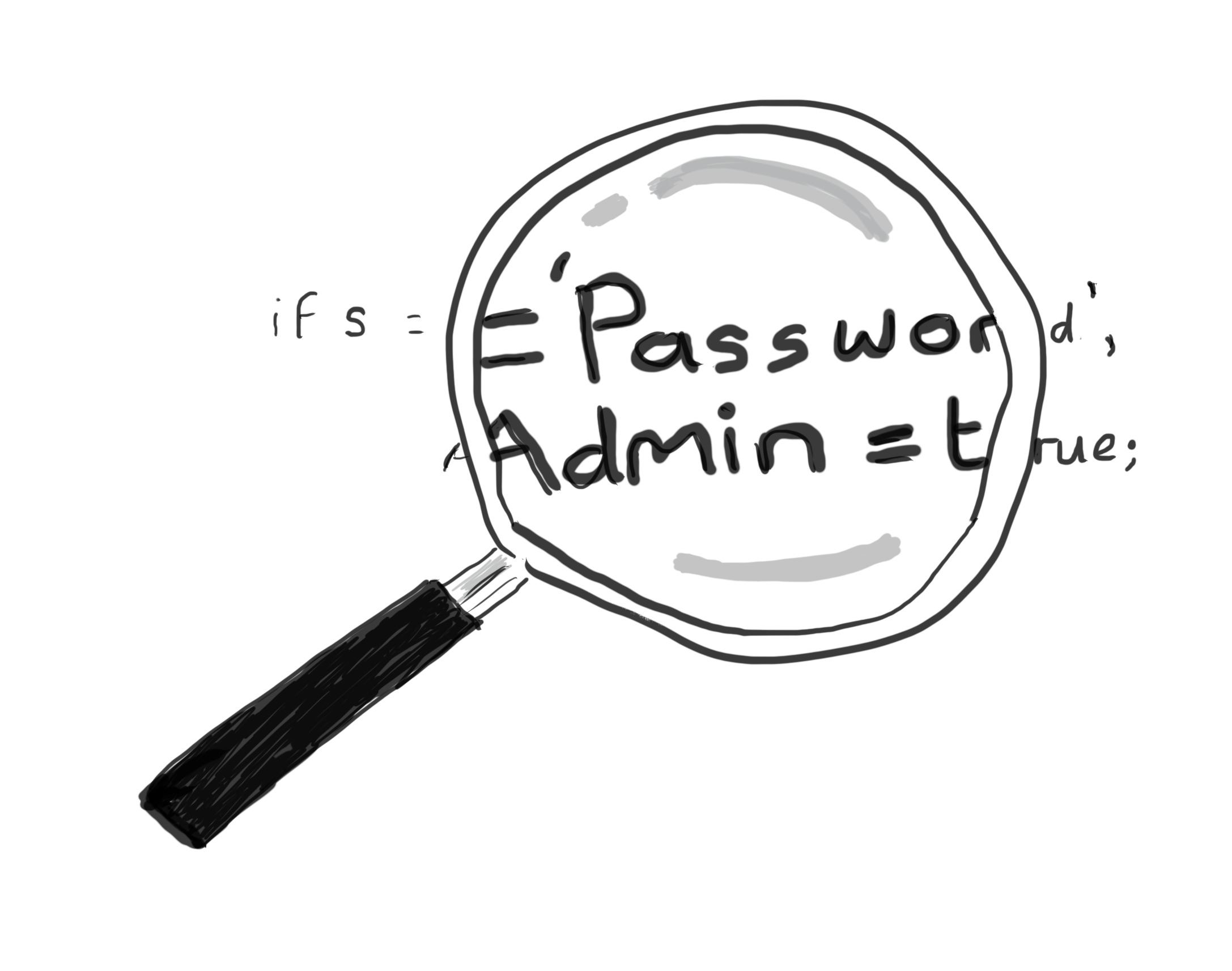
Password hell!
You know what it’s like, you have just hit the ‘Register’ button on a website and you’re being asked to provide a password to set up an account. So you try to come up with something that you can remember and meets the website’s password policy which dictates the characters to use and its minimum…
-

Customer data: a moral obligation to keep it secure
Data is big! Big data is even bigger! Organisations across the world collect a lot of it: customer data, employee data, supplier data, competitor data. Organisations collect customer data in order to gain advantage over their commercial rivals. They use it to learn how customers spend money: which products they are likely to buy based…
-

Agile – 5 mistakes organisations make
Introduction When I first encountered the Agile framework, I was awestruck by how software engineering teams worked so differently from what I had been used to and achieved much better results than I had seen before. I saw developers work in groups of two or three at the same workstation for hours on end, I…
-

Sophisticated attack? Really?
Listen to a news report or read a news headline in the paper about a security breach and you are likely to hear from the affected company that it was a victim of a sophisticated attack. The reason for this is simple: no-one wants to admit that they were actually the victim a rather simple…